Last Updated on 2024-11-28
Numerous challenges and threats can affect the future of software engineering. Though some of these challenges also offer opportunities for innovation and growth, it is essential to address them for the continued success of the field.
Thus, the software engineering community must remain vigilant and proactive in identifying and addressing these challenges to maintain productivity. Doing so will help sustain the field’s growth. It also ensures the continuous delivery of high-quality software solutions that meet the needs of users and organizations alike.
The Rising Software Security Issues
The security threats in software engineering are constantly changing and can happen at any stage of software development. Software engineers must use secure coding practices, perform regular security assessments, manage vulnerabilities, and provide ongoing security awareness training to ensure security.
To mitigate threats, it’s important to take proactive measures, monitor continuously, and promote collaboration between development and security teams.
The Critical Role of Software Engineering in the Digital Age
In the digital age, software engineering is akin to a superpower—constructing the digital infrastructure that powers everything from mobile apps to space exploration. Yet, with great power comes great responsibility. Engineers also face a landscape rich with risks and adversaries as they build the world’s technological wonders.
The Continuous Evolution of Software Security Threats
The continuous evolution of software security threats is an ongoing challenge that organizations and individuals face in the digital landscape. The threat landscape constantly changes as cybercriminals adapt tactics to exploit vulnerabilities and emerging technologies.
Understanding the Stakes for Tomorrow’s Software Infrastructure
Understanding the stakes for tomorrow’s software infrastructure work is critical as the digital landscape evolves rapidly. Tomorrow’s software infrastructure will be pivotal in shaping the technological landscape, influencing innovation, economic growth, and the overall well-being of individuals and organizations.
Anticipating Future Risks of Software Development: A Proactive Stance
This calls for more than a reactive approach. Anticipating future challenges is fundamental to safeguarding software integrity and functionality.
Software engineers must shift their mindset to vigilance and foresight, looking for potential threats before they materialize. By continuously scanning the horizon for new risks and staying adept with emerging technologies, you prepare to defend and strengthen your software against looming challenges proactively.
Below are some of the major risks of software development that software engineers need to prepare for.
Threat #1: AI-Powered Cyberattacks
As artificial intelligence (AI) continues to advance, there is growing concern about its potential use in cyberattacks. AI-powered cyberattacks leverage machine learning algorithms, automated systems, and sophisticated analytics to enhance malicious activities’ efficiency, sophistication, and adaptability.
The analytics embedded within these AI systems can predict and identify potential vulnerabilities at an unprecedented scale.
Understanding AI-Driven Threat Complexity
AI-driven threats are transforming the cybersecurity battlefield. These sophisticated attacks leverage artificial intelligence to create malware that can learn and adapt, making detection and defense increasingly complex.
With AI, threats can evolve in real-time, efficiently identifying and exploiting vulnerabilities. Understanding this complex threat landscape is essential; it’s a world where attacks are not just automated but intelligent and constantly learning from their environment to maximize impact.
Preemptive Strategies for Combating AI Exploits
A proactive defense strategy is imperative to combat AI exploits, potentially involving technologies like OpenAI. Invest in AI security posture management solutions capable of real-time anomaly detection and smart authentication.
Develop comprehensive playbooks for threat response, considering AI’s role, including the nuances of advanced platforms like OpenAI and updating them with evolving best practices. And remember: rigorously question vendor claims—ensure that any AI security tool you consider integrates well with your existing systems and enhances your defense capabilities.
- AI Threat Response Playbook: Implement and regularly update AI-specific threat response strategies.
- Real-Time Anomaly Detection: Invest in tools to identify unusual patterns indicative of AI-driven attacks.
- Smart Authentication Systems: Transition from vulnerable authentication methods to more secure options like passwordless systems.
- Vendor Due Diligence: Approach vendor claims skeptically and verify the effectiveness of AI security solutions.
- Training and Awareness: Educate your team about AI threats and conduct regular training sessions to stay current with AI security trends.
Addressing the threats posed by AI-powered cyberattacks requires a multi-faceted approach involving the development of robust AI-powered cybersecurity solutions, continuous monitoring, user awareness training, and implementing defense mechanisms that can adapt to evolving attack strategies.
Collaboration between cybersecurity experts, researchers, and the wider technology community is crucial to staying ahead of the evolving landscape of AI-driven cyber threats, which constantly shape cybersecurity trends.
Threat #2: Compromised Supply Chains
A compromised supply chain typically introduces malicious or vulnerable components into the software development and deployment process. This can happen at various stages of the software development life cycle, resulting in serious consequences for the final product’s security and integrity.
Navigating the Risks of Third-Party Dependencies
Navigating the risks of third-party dependencies is akin to walking on a tightrope. It requires balance, precision, and a clear understanding of the pitfalls below.
It’s critical to employ thorough vetting processes, continuous monitoring, and robust security protocols to ensure that third-party code doesn’t introduce vulnerabilities. Relying on a comprehensive inventory of third-party components and understanding their security postures can help manage these risks effectively.
Transparency from vendors about their security measures is key; if they can’t provide it, one may need to consider alternative solutions.
- Conduct extensive security audits on third-party services before integration.
- Set up automated tools for continuous monitoring of third-party dependencies for vulnerabilities.
- Create strict access controls and sandbox environments for external components.
- Maintain an updated inventory of all third-party dependencies and their licenses, vulnerabilities, and patches.
- Establish strong partnerships with vendors for transparent communication regarding security.
Security awareness and education for developers are parts of a comprehensive strategy to address these challenges. This includes proper management of sensitive credentials and implementing robust security policies.
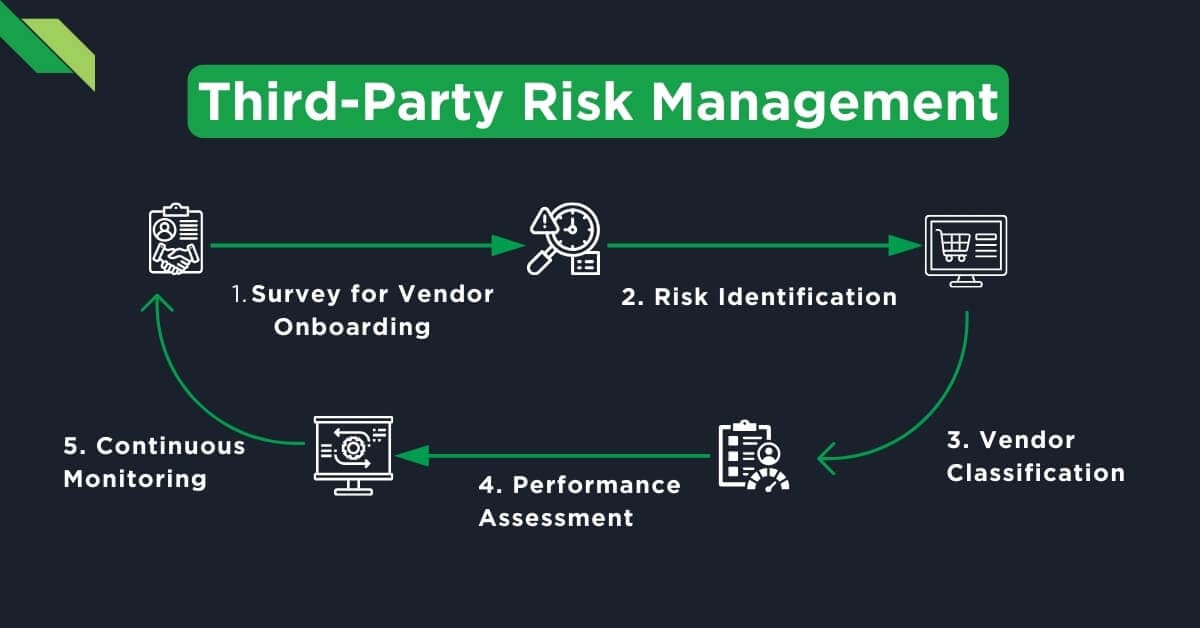
Frameworks for Ensuring Secure Software Supply Chains
Frameworks for securing software supply chains are essential scaffolding in any security architecture. This involves adopting established standards like the NIST cybersecurity framework and tailored strategies like the Software Supply Chain Levels for Software Artifacts (SLSA). Implementing such frameworks means:
- Automating verification processes to check the integrity of third-party software and updates.
- Ensuring version control and approving only trusted sources and code repositories.
- A software bill of materials (SBOM) will be deployed to provide visibility into the components used.
- Encouraging strong end-to-end encryption and secure authentication mechanisms in all supply chain transactions.
- Regularly auditing suppliers and insisting on adherence to security benchmarks.
Remember, frameworks are not just set-and-forget solutions. They require continuous refinement and adaptation to stay ahead of emerging threats.
Threat #3: Cloud Vulnerabilities
Cloud computing offers scalability, flexibility, and cost-effectiveness, particularly when managing databases.
However, it also poses new challenges and potential vulnerabilities around database security. Businesses must be aware of these concerns to ensure the safety of their data and operational security.
Organizations can leverage cloud computing to manage their workloads while minimizing risks by implementing robust security measures and staying updated with emerging threats.
Protecting Emerging Cloud-Native Applications
The emergence of cloud-native applications has redefined how you must protect modern software. These applications, designed specifically for cloud environments, demand meticulous attention to security in both deployment and operation. That means embracing principles such as immutability, where systems are replaced rather than changed, enforcing strict API gateways, and applying least privilege access controls.
Automation plays a key role here. It ensures that security policies are consistently applied across the entire infrastructure.
- Prioritize security in the design phase with the principle of Least Privilege and Secure by Design.
- Implement robust identity and access management (IAM) protocols for users and services.
- Leverage container orchestration tools like Kubernetes with integrated security features.
- Utilize continuous monitoring and vulnerability scanning to catch risks early.
- Apply regular updates and patches as part of a CI/CD pipeline to minimize exploit windows.

Addressing Configuration Mistakes and Data Privacy
Configuration mistakes and data privacy are intertwined challenges that can undermine cloud security.
It’s critical to embrace a “shift-left” mindset, where security is integrated early in the development process, not tacked on after.
Automation can help enforce best practices and requires human oversight to catch misconfigurations that machines might miss. Consider implementing policy as code, specifying configurations that automatically apply across your infrastructure.
Constantly educate your team on data privacy laws and best-practice handling protocols to ensure that your configurations safeguard sensitive information.
- Audit configurations regularly with automated tools that can identify and remediate discrepancies.
- Develop and enforce clear data management policies that comply with privacy regulations like GDPR and CCPA.
- Effective cookie management is also essential, as it helps control data collection and ensures compliance with privacy regulations.
- Utilize policy-as-code frameworks for maintaining consistency and compliance.
- Run periodic training sessions for employees on the importance of securing data.
- Encourage a culture of security mindfulness, where each team member feels responsible for data privacy.
Organizations can reduce the risk of configuration mistakes that may compromise data privacy. Addressing misconfigurations requires a holistic approach that involves technical controls, staff education, and a commitment to ongoing improvement in security practices.
Threat #4: Advanced Phishing Techniques
Advanced phishing techniques pose significant threats to individuals and organizations.
They exploit sophisticated methods to deceive users and gain unauthorized access to sensitive information. They also open doors to ransomware attacks. These techniques often go beyond traditional phishing methods, making them more difficult to detect and thwart.
Evolution of Social Engineering Attacks on Engineers
Social engineering attacks have become highly sophisticated, targeting not just individuals but specifically engineers with access to critical systems.
Attackers now craft intricate backstories, often impersonating trusted sources, to manipulate or trick engineers into compromising security. Understanding the threat landscape’s evolution becomes essential as these schemes become more elaborate, including deepfake technology and AI-generated content.
Engineers must be equipped to recognize subtle cues of deception and maintain a healthy level of skepticism, especially when requests involve access to sensitive data or systems.
- Stay informed about the latest social engineering tactics through continuous education.
- Emphasize verification processes before granting access or making changes to systems.
- Foster a culture where it’s acceptable to question and double-check suspicious requests.
- Encourage cross-communication within teams when any request seems out of ordinary patterns.
- Simulate social engineering scenarios to provide practical experience in recognizing and responding to them.
Organizations must prioritize cybersecurity training, implement strong authentication mechanisms, regularly update security policies, and use advanced cybersecurity solutions to prevent social engineering attacks and keep abreast of cybersecurity trends.
Educating engineers about the latest social engineering tactics and promoting a culture of cybersecurity awareness is crucial in mitigating risks associated with these threats.
Empowering Teams to Recognize and Resist Phishing Scams
Empowering your teams to recognize and resist phishing scams isn’t just a technical challenge—it’s an educational one. Integrate email authentication protocols into your security measures to bolster your defense.
Create a culture where healthy skepticism is encouraged and provide regular, up-to-date training sessions highlighting the latest phishing techniques, including the significance of email authentication. Make sure every member knows what red flags to look for and understands the importance of reporting potential threats. Use simulated phishing exercises to provide practical experience and reinforce learning.
Remember, knowledge is their shield. By incorporating email authentication and keeping your team well-informed, they become a formidable first line of defense against these deceptive threats.
- Integrate anti-phishing training into the regular security awareness programs.
- Simulate phishing attacks to give practical experience in identifying scams.
- Establish clear reporting channels for employees to communicate potential phishing incidents.
- Update training content regularly to include the latest tactics used by scammers.
- Encourage a no-punishment policy for reporting, even if mistakes are made.
By combining these strategies, organizations can create a more resilient workforce better equipped to recognize and resist phishing scams.
Threat #5: Low-Code/No-Code Security Oversight
Low-code and no-code development platforms have gained popularity for enabling individuals with limited coding skills to create software applications quickly, thereby enhancing developer productivity. However, using these platforms can introduce unique security challenges that organizations must address.
Balancing Accessibility with Risk in Low-Code Solutions
Low-code/no-code solutions have democratized software development, making it accessible to non-coders. However, balancing the convenience they offer with potential security risks is critical. It’s essential to establish clear governance policies defining who can create what and to ensure robust security measures are integrated.
Transparency over how these platforms manage data security is a must. Encourage teams to customize security settings to fit organizational needs without relying solely on default configurations. This balanced approach can harness the benefits of low-code/no-code development while maintaining an acceptable level of risk.
- Develop a governance framework to identify who can use low-code tools and for which projects.
- Customize security settings in low-code platforms beyond default configurations to meet specific organizational needs.
- Involve IT security in vetting and selecting low-code/no-code platforms.
- Educate citizen developers on security best practices tailored to low-code environments.
- Regularly review and update the security measures as platforms evolve and organizational needs change.
Balancing accessibility with risk in low-code solutions requires a holistic and proactive approach to security. By implementing these considerations, organizations can leverage the benefits of low-code development while effectively managing and mitigating associated risks.
Lastly, organizations should evaluate proxies pricing models to ensure cost-effective solutions for monitoring and securing data traffic in low-code/no-code applications.
Instituting Robust Security Protocols Amidst Democratized Development
As development becomes more democratized with the proliferation of low-code/no-code platforms, instituting robust security protocols, including effective login measures, is crucial.
Organizations must enforce security measures such as rigorous password policies, two-factor authentication for logins, regular security audits, and role-based access controls that every employee, irrespective of their technical background, can understand and implement.
Integrating security training into the organizational culture is also beneficial, ensuring that every team member, not just developers, knows the security implications of their actions.
- Implement universal security policies for all platforms, including low-code/no-code tools.
- Regularly update and audit security protocols to patch vulnerabilities.
- Conduct role-based security training to cater to different levels of technical expertise.
- Use monitoring tools to oversee activities on democratized development platforms for unusual behavior.
- Designate responsibility for security within teams to ensure that best practices are followed.
Organizations can enhance the security posture of applications developed using low-code and no-code platforms, minimizing the risk of vulnerabilities and ensuring compliance with security standards. Treating low-code/no-code development with the same security diligence as traditional coding practices is essential.
Threat #6: Quantum Computing Breakthroughs
While quantum computing offers exciting possibilities for solving complex problems, it also raises potential threats and challenges to traditional cryptographic methods, such as those used in blockchain technology and software development practices.
Potential Impact on Encryption Standards
The advent of quantum computing harbors the potential to upheave current encryption standards, rendering traditional cryptographic methods like RSA and ECC vulnerable. Quantum computers possess the computational might to break these encryptions, potentially exposing data to new security risks.
Enterprises and government organizations are taking note, propelling a surge in research for quantum-resistant algorithms. These new paradigms for encryption are centered on complexity that even quantum computers will find intractable, thereby ensuring the continued confidentiality and integrity of sensitive data.
- Understand the basics of how quantum computing challenges existing cryptographic algorithms.
- Begin an assessment of organizational encryption methods with an eye toward potential quantum vulnerabilities.
- Proactively monitor the progress in quantum-resistant cryptographic standards and start planning for integration.
- Engage with cryptographic experts to stay abreast of developments in post-quantum cryptography.
- Prioritize data that requires long-term confidentiality to address with quantum-resistant strategies first.
Organizations should stay informed about the progress of quantum computing, participate in standardization efforts for quantum-resistant cryptography, and plan for the eventual migration to encryption standards that can withstand the power of quantum computers.
Preparing for Post-Quantum Crypto Landscape
Preparing for a post-quantum crypto landscape entails forward-thinking strategies to stay ahead of the curve. Begin by assessing which data and systems will be most at risk when quantum capabilities become widespread.
Update cryptographic protocols with algorithms currently being developed for quantum resistance. Engage in industry partnerships and collaborative efforts to shape and adopt new standards.
Educate your team on quantum developments and the importance of future-proofing security. It’s a balance of deploying what’s proven today while preparing for the encryption needs of tomorrow.
- Incorporate quantum-resistant algorithms into your security roadmaps.
- Participate in forums discussing the post-quantum cryptography standards.
- Review and revise current encryption-dependent systems and practices.
- Encourage ongoing education about quantum computing and post-quantum cryptography.
- Develop a transition plan for when quantum-safe algorithms are standardized and ready to be deployed.
By taking a proactive and informed approach to preparing for a post-quantum cryptographic landscape, organizations can enhance their resilience against potential quantum threats and ensure the security of their sensitive information in the long term.
Regularly reassess your cryptographic strategy in light of advancements in quantum computing and emerging quantum-resistant cryptographic standards.
Threat #7: IoT and Device Ecosystem Disruptions
The Internet of Things (IoT) and the broader device ecosystem have the potential to bring about significant disruptions across various industries, including the healthcare industry. As more devices become connected and intelligent, new opportunities and challenges emerge, particularly in the healthcare industry, where IoT can revolutionize patient care and operational efficiency.
Mitigating the Increasing Rift in IoT Security
Mitigating the rift in IoT security requires a multi-faceted approach to address the diversity and volume of devices connected to the network. Begin by embracing a security-by-design philosophy, ensuring that security isn’t an afterthought but a cornerstone of your IoT strategy.
Encourage manufacturers to harden their devices against attacks, enforce strong default settings, and make regular firmware updates effortless for users. Implement network segmentation to isolate IoT devices from critical business systems, reducing the risk of cross-contamination.
Additionally, practice regular device audits and monitor device behavior for anomalies that could indicate a breach.
- Establish Security by Design principles during the IoT device development phase.
- Advocate for and adopt industry standards and certifications for IoT security.
- Leverage network segmentation to limit the IoT devices’ access to sensitive information.
- Maintain an up-to-date inventory of all IoT devices and their security status.
- Monitor IoT device activity for irregular patterns hinting at a cybersecurity threat.
To secure IoT, take a proactive approach that covers device design, deployment, and ongoing management. This strengthens the security of IoT ecosystems and protects against evolving threats.
Best Practices for Securing Connected Environments
Securing connected environments involves a strategic set of best practices that fortify an expansive network of interconnected devices. These best practices include:
- Consistent Application of Updates: Regularly apply patches and firmware updates to IoT devices to address vulnerabilities promptly.
- Strong Authentication Methods: Utilize multi-factor authentication to ensure only authorized devices and users gain network access.
- Encryption of Data in Transit: Use robust encryption protocols to protect data as it moves across the network.
- Device Configuration Management: Implement tools for centralized management to maintain consistent security settings across all IoT devices.
- Incident Response Preparedness: Have a clear incident response plan for potential IoT breaches, including containment and recovery procedures.
The ultimate aim is a holistic, layered security strategy that mitigates risks and safeguards the integrity of the interconnected environment.

Poor cyber hygiene practices can significantly contribute to cybersecurity vulnerabilities, increasing the risk of cyber threats and cybercrime. Cyber hygiene involves good security practices to safeguard digital systems, data, and networks.
Fostering A Culture of Security First Among Engineers
Fostering a “Security First” culture among engineers involves ingraining security consciousness into every software development life cycle aspect. This can be achieved through regular training and knowledge-sharing sessions and by making security a key project performance indicator.
Engineers should be motivated to stay updated with security trends and best practices. Encourage a proactive approach where security considerations are integral to the planning and design stages rather than an afterthought. Reward vigilance and identify security issues to solidify the mindset that security is everyone’s responsibility.
- Integrate security into the onboarding process for all engineering staff.
- Organize hackathons focused on discovering and resolving security vulnerabilities.
- Host regular ‘lunch and learn’ sessions led by security experts or team members who share insights on current security topics.
- Establish a security champions program to lead by example and mentor others within the team.
- Implement a recognition system to incentivize and recognize proactive security contributions.
Organizations can cultivate a culture of security first among engineers, leading to more resilient and secure software systems. Emphasizing the importance of security throughout the development lifecycle and fostering a sense of shared responsibility contribute to a proactive and effective security mindset among engineering teams.
Continuous Education and Training on Software Development Security Essentials
Continuous education and training on security essentials is not just a line item on the agenda—it’s a perpetual commitment to safeguarding the enterprise.
Encourage engineers to engage regularly with updated security training modules that cover a spectrum of threats and defensive techniques. Host interactive workshops and cyber drills that simulate actual attack scenarios.
Make sure to include lessons on the latest regulations and compliance requirements, as these often influence how security should be approached. Such an approach ensures that an engineer’s knowledge remains fresh, relevant, and sharp–ready to protect your software and systems against the ever-evolving threat landscape.
- Schedule ongoing security training sessions to cover new threats and defense tactics.
- Run live cyber attack simulations for hands-on experience in threat mitigation.
- Update educational content with the latest compliance laws and security protocols.
- Create an accessible repository of security learning resources for self-paced learning.
- Encourage certification courses in cybersecurity as part of professional development.
Adopt a holistic and ongoing security education and training approach to empower employees to identify and mitigate security risks proactively. Regularly updating training content and incorporating diverse learning methods contribute to building a resilient workforce capable of defending against evolving cybersecurity threats.
Threat #9: Regulatory Compliance Challenges
Compliance with regulations is a critical part of software engineering. It involves following laws, standards, and guidelines for software development, deployment, and use. Although compliance is essential for legal and ethical reasons, it can be challenging for software engineers.
Keeping Pace with Global Cybersecurity Regulations
In a world where cybersecurity regulations shift as quickly as the threats they aim to combat, keeping pace is both a challenge and a necessity. You must monitor global cybersecurity developments and analyze how they impact your operations.
Adapt your policies and protocol to comply not just for legal adherence but to uphold a standard of trust with your users. Engagement with legal experts and cybersecurity consultants ensures that you not only meet the minimum requirements but excel in protecting your stakeholders’ data.
Additionally, participation in industry forums can keep you apprised of changes on the horizon.
- Establish a compliance team dedicated to tracking and implementing regulatory updates.
- Foster relationships with legal experts specializing in global cybersecurity law.
- Engage in cybersecurity forums and conferences to stay informed on regulatory trends.
- Review and refine your incident response and data management policies to align with new regulations.
- Develop a compliance checklist tailored for software engineering processes.
To keep up with cybersecurity regulations worldwide, being proactive and working with cross-functional teams is important. Ongoing education and staying informed about the constantly changing regulatory landscape is key. Regular assessments, continuous monitoring, and following best practices all contribute to a strong and compliant cybersecurity approach.
Consequences of Non-Compliance for Software Projects
The fallout of non-compliance with cybersecurity regulations for software projects can be grave. They range from hefty fines, which can strangle company finances, to reputational damage that erodes user trust and deters potential clients.
Furthermore, non-compliance can lead to legal action and increased scrutiny from regulators, hindering future business opportunities. In severe cases, the fallout from non-compliance may even result in service shutdowns or limitations on operations. To avoid these pitfalls, it is vital to have solid compliance strategies in place and adhere to them diligently.
- Financial penalties resulting from fines can impact your company’s bottom line.
- Reputational damage could lead to a loss of customer trust and a reduction in market share.
- Legal challenges may arise, consuming resources and time to resolve.
- Regulator scrutiny might increase, affecting your ability to conduct business smoothly.
- Possible operational shutdowns or constraints.
Organizations should prioritize cybersecurity compliance to mitigate these consequences, regularly assess their adherence to relevant regulations, and proactively address gaps or vulnerabilities. Implementing robust cybersecurity measures and fostering a culture of compliance is essential for safeguarding software projects and maintaining the trust of stakeholders.
Threat #10: Lack of Skilled Cybersecurity Professionals
The shortage of skilled cybersecurity professionals is a significant challenge facing organizations today. As cyber threats evolve and increase in complexity, the demand for qualified cybersecurity experts has surged.

Addressing the Cyber Security Skills Gap
Addressing the cybersecurity skills gap is akin to solving a critical puzzle in safeguarding our digital future. As the demand for skilled professionals outstrips supply, organizations must become more inventive in their approach.
This could include developing internal upskilling programs, offering apprenticeships, and creating a culture that encourages continuous learning. Partnerships with educational institutions for a steady stream of talent and inclusivity initiatives to widen the recruitment net also play a vital role.
Ultimately, bridging this gap isn’t just about hiring; it’s about nurturing and retaining the skills within your workforce.
- Invest in training programs to upskill current employees in cybersecurity.
- Collaborate with educational institutions to align curriculum with industry needs.
- Create an inclusive work environment that attracts diverse cybersecurity talent.
- Offer competitive benefits and continuous career development opportunities to retain skilled professionals.
- Engage with professional cybersecurity communities to stay informed and connected with talent.
Addressing the cybersecurity skills gap requires a multifaceted approach that combines education, training, collaboration, and strategic workforce planning. By adopting these strategies, organizations can build a strong and capable cybersecurity workforce to navigate today’s threat landscape challenges.
Recruiting and Retaining Expertise in a Competitive Market
In the highly competitive market of cybersecurity expertise, successful recruiting and retention hinge on a company’s ability to stand out. Offer compelling career paths that promise growth, continuous learning opportunities, and the chance to work on cutting-edge projects.
Also, consider remote and flexible work arrangements to appeal to a broader talent pool. Build a company culture that not only values but invests in its employees’ development and well-being. Recognition, competitive salaries, and benefits tailored to individual needs are also key.
Companies that treat their cybersecurity professionals as invaluable assets will not only attract but, more importantly, retain the top talent necessary to guard their digital fortresses.
- Highlight career progression opportunities and continuous education in job listings.
- Foster a company culture that values work-life balance and respects personal time.
- Focus on competitive compensation packages that acknowledge the value of cybersecurity expertise.
- Provide platforms for employees to innovate and contribute to thought leadership in cybersecurity.
- Prioritize employee wellness with benefits such as mental health support and stress management programs.
By combining effective recruiting strategies with retention efforts, organizations can attract top cybersecurity talent and create an environment where professionals are motivated to stay and contribute to the organization’s security objectives. Regularly reassess and adjust these strategies to align with evolving industry dynamics and the needs of cybersecurity professionals.
Proactive Measures Are Key for Software Security Threats Preparedness
Adopting a proactive approach helps organizations identify and address security issues before they escalate, reducing the risk of security breaches and data compromises.
Introduction to Future Security Risks in Software Development
As software engineering propels forward, innovating, anticipating, and preparing for future security risks is essential. As cyber threats become more advanced and intertwined with the very fabric of technology, engineers must arm themselves with knowledge and tools to navigate this complex landscape.
It’s about building a resilient digital ecosystem that can withstand the onslaught of potential risks, ranging from AI and machine learning exploits to vulnerabilities brought by the quantum computing era.
It’s a time when staying informed, vigilant, and proactive isn’t just a recommendation—it’s necessary to ensure the safe and trustworthy development of software that plays a crucial role in our lives.
The Evolving Sphere of Software Development
Software development is continuously evolving, shaped by technological advancements, changing market demands, and the relentless ingenuity of threat actors.
Engineers must grapple with new programming paradigms, platforms, like Python, and integration challenges, often under pressure to deliver faster and more seamlessly than ever before. Beyond technical acumen, a keen situational awareness of these innovations’ security implications becomes imperative.
To flourish in this dynamic field, embracing a continuous learning and adaptation culture is as critical as the code you write.
The Paramount Importance of Cyber Resilience
Cyber resilience, including specific resilience measures, has become a linchpin in software engineering. It underlines the shift from a purely defensive security posture to a more robust strategy that includes response and recovery.
The ability to operate during and bounce back from cyber incidents quickly is as important as preventing such incidents. With the understanding that no defense can be impregnable, organizations are now weaving resilience into the fabric of their software development life cycle.
Investing in resilient architectures, backup systems, employee training, and comprehensive incident response plans ensures that your organization can withstand and adapt to cyber threats, supporting continuous operation and safeguarding your reputation.
Build A Secure Software with Full Scale
Are you planning to build your software development team but struggling to find the right talent in the tech sector? You’re not alone, as there is an ongoing shortage of IT workforce.
But don’t worry. Full Scale can help you find your team’s most qualified technical personnel. We aim to make the recruitment process as seamless as possible for you.
Our team of experts will handle the entire recruitment procedure for you so you can focus on growing your business. We have a thorough screening process for software engineers, testers, project managers, and marketing specialists, which helps to expedite your recruitment process.
With Full Scale, you can quickly build your team, which is well-versed and experts in building secured software.
Start Building A Secure Product Today!
FAQs: Arm Yourself with Expert Insights
Here are some frequently asked questions about software engineering security threats:
How Can Organizations Build Resilience Against These Software Development Issues?
To prevent and protect against security threats in software engineering, adopting a multi-dimensional approach involving people, processes, and technologies is vital. This means taking proactive, adaptive measures to reinforce security at every software development life cycle stage.
By doing so, organizations can mitigate the potential damage of an attack and increase their ability to recover from security incidents. This requires constant improvement of security measures and a commitment to integrating security as a core aspect of software development.
Ultimately, the goal is to build a culture of resilience and security awareness within the organization so that everyone, from developers to end-users, understands the importance of security and takes an active role in safeguarding against risks.
What Are the Best Resources for Navigating Future Risks in Software Development?
Navigating future risks in software engineering requires staying informed about emerging trends, threats, and best practices. Here are five valuable resources to help you navigate future risks in software engineering:
- MITRE ATT&CK Framework: A knowledge base that comprehensively maps the tactics and techniques used by cyber adversaries. It is an excellent resource for understanding the evolving landscape of cyber threats and tactics.
- OWASP (Open Web Application Security Project): A community-driven organization that focuses on improving software security. Their resources include guides, tools, and projects that address common vulnerabilities and emerging threats in web applications and software development.
- NIST Cybersecurity Framework: NIST’s Cybersecurity Framework is a set of guidelines, standards, and best practices that help organizations manage and improve their cybersecurity risk management processes. It’s a valuable resource for building resilience against evolving cyber threats.
- SANS Internet Storm Center (ISC) Diary: Maintained by the SANS Institute, it provides daily diary entries written by cybersecurity experts. It covers current threats, vulnerabilities, and incidents, offering insights into the evolving landscape of cybersecurity.
- SecurityWeek: A comprehensive source for cybersecurity news, analysis, and insights. It covers a wide range of topics, including threat intelligence, vulnerabilities, and emerging trends in the cybersecurity landscape.
Regularly consulting these sources will help you stay ahead of the latest developments and risks in software engineering and cybersecurity.

Matt Watson is a serial tech entrepreneur who has started four companies and had a nine-figure exit. He was the founder and CTO of VinSolutions, the #1 CRM software used in today’s automotive industry. He has over twenty years of experience working as a tech CTO and building cutting-edge SaaS solutions.
As the CEO of Full Scale, he has helped over 100 tech companies build their software services and development teams. Full Scale specializes in helping tech companies grow by augmenting their in-house teams with software development talent from the Philippines.
Matt hosts Startup Hustle, a top podcast about entrepreneurship with over 6 million downloads. He has a wealth of knowledge about startups and business from his personal experience and from interviewing hundreds of other entrepreneurs.





