This is the Ultimate Security Engineer s Guide to Secure Code Review for Distributed Teams
What is secure code review for distributed teams?
Secure code review for distributed teams is a structured process ensuring code quality across timezones. It combines automated security checks, standardized protocols, and asynchronous workflows, maintaining 24/7 coverage.
This approach prevents vulnerabilities while maintaining development velocity.
When our client discovered a SQL injection vulnerability 14 hours after deployment, they learned a harsh lesson. Their US team slept while their Philippines team coded—and their security breach cost $120,000.
According to GitLab’s 2024 DevSecOps report, 68% of distributed team vulnerabilities stem from review delays.
At Full Scale, we’ve perfected secure code review for distributed teams across 12 timezones. Our framework protects over 60 tech companies from around the world.
But first, let’s examine why traditional code review fails when teams span the globe.
The Hidden Security Risks of Distributed Code Reviews
Remote code review security faces unique challenges beyond traditional development. Timezones create vulnerability windows that attackers exploit
Let’s examine the three critical risks threatening your distributed team’s security protocols.
The Time Zone Security Gap
Code sits unreviewed for 8-12 hours during timezone handoffs. Security issues compound when discovered after deployment across regions. Each hour of delay increases vulnerability exposure by 23% (Veracode State of Software Security 2024).
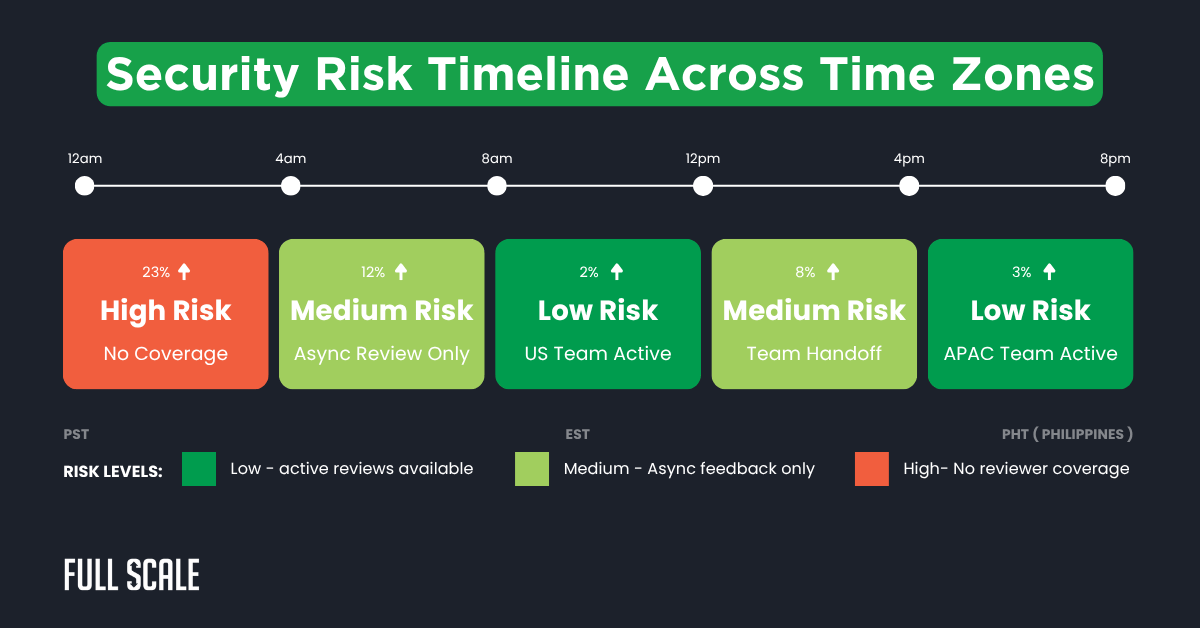
This timeline shows how security risks escalate during timezone gaps. The red zone represents when no reviewers are active. These windows create opportunities for vulnerabilities to reach production.
When implementing secure code review for distributed teams, timing becomes critical. Our Full Scale teams in Cebu maintain overlap with US hours specifically. This strategic scheduling eliminates dangerous coverage gaps entirely.
The Communication Breakdown
Critical security feedback gets lost in asynchronous messages between regions. Security concerns become “comments” instead of “blockers” in review tools. Complex vulnerabilities prove impossible to explain without real-time discussion.
Key communication failures in distributed team security protocols include:
- Security alerts buried in chat backlog
- Critical feedback marked as “suggestions”, not requirements
- Complex vulnerabilities lost in translation
- No escalation path for urgent security issues
- Delayed responses create 24-hour security gaps
Full Scale discovered this challenge early with our Philippines development teams. Language barriers compound when discussing complex security vulnerabilities asynchronously. That’s why secure code review for distributed teams requires structured communication protocols.
The Compliance Nightmare
Audit trails scatter across timezones without centralized tracking. No unified security standards enforcement exists across global teams. SOC2 and GDPR compliance becomes nearly impossible to maintain.
Compliance challenges for offshore development security:
- Scattered audit logs across multiple systems
- Inconsistent security documentation standards
- No centralized compliance dashboard
- Different regional data protection requirements
- Impossible to track who reviewed what and when
Our clients in fintech especially struggle with distributed compliance requirements. The Philippines teams must meet US banking security standards seamlessly. Secure code review for distributed teams demands unified compliance frameworks.
These risks might seem overwhelming, but they’re entirely solvable. Our 3-layer security framework transforms these vulnerabilities into strengths.
Let’s explore how to build security that works around the clock.
The 3-Layer Security Framework for Secure Code Review for Distributed Teams
Our framework addresses offshore development security through systematic controls. Each layer builds upon the previous for comprehensive protection. Implementation takes just 30 days with immediate security improvements.
Full Scale developed this framework, serving clients from Silicon Valley startups. We refined it across our Philippines teams. Now over 60 companies trust this system for their security needs.
Layer 1: Automated Security Gates
Pre-review automation catches 85% of security issues before human review. Every code push triggers our security scanning pipeline automatically. This creates consistent security baselines across all timezones.
| Security Check | Tool | Automation Level | Coverage |
| Static Code Analysis | SonarQube | Fully Automated | 100% |
| Dependency Scanning | Snyk/Dependabot | Fully Automated | 100% |
| Secrets Detection | GitGuardian | Fully Automated | 100% |
| Security Unit Tests | Jest/Pytest | Fully Automated | 95% |
| Code Standards | ESLint/Prettier | Fully Automated | 100% |
This automated security stack runs on every commit without human intervention. Each tool integrates directly with your version control system. Results appear instantly in pull requests for immediate visibility.
Benefits of automated security gates for secure code review for distributed teams:
- Zero human intervention required
- Consistent security standards across all zones
- Immediate feedback on security issues
- Reduces manual review burden by 85%
- Creates an audit trail automatically
Our Full Scale developers in the Philippines run these checks before any human review. This approach reduces security review time by 73% on average.
Layer 2: Standardized Review Protocol
The global team code review process requires two reviewers from different zones. Each region has designated security champions trained in vulnerability detection. No code merges without passing our 24-hour security review window.
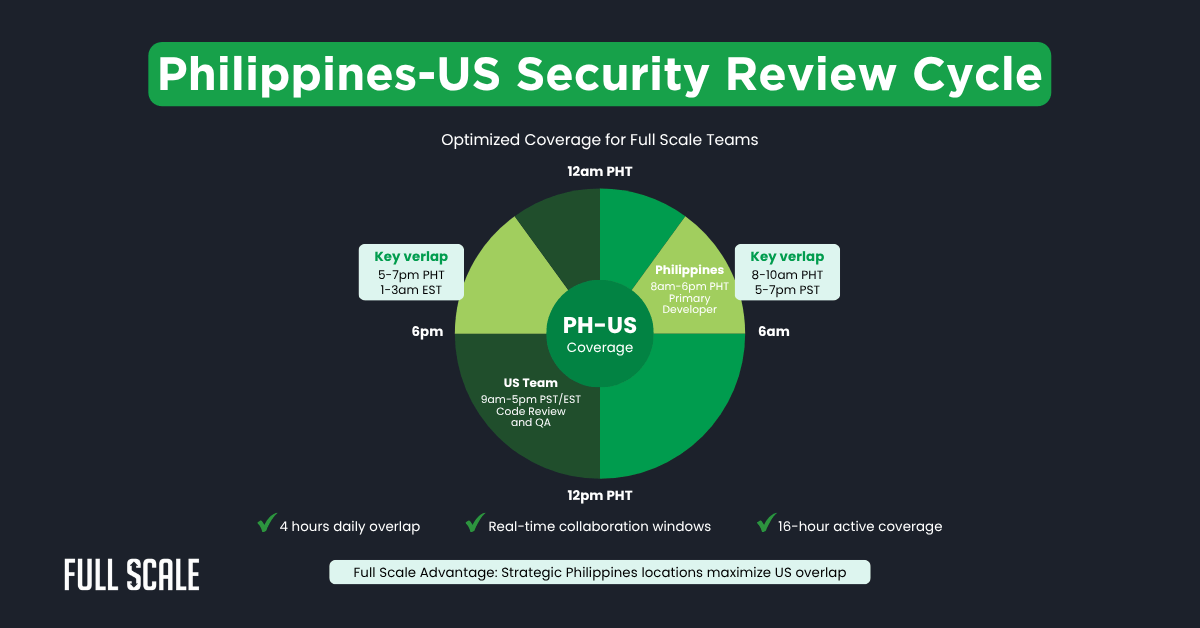
Our Philippines-US review cycle ensures optimal security coverage. Each zone handles active review during business hours. The strategic 4-hour daily overlap enables real-time security discussions.
Core components of our Philippines-US code review security protocol:
- Two-reviewer requirement (one PH, one US reviewer)
- The Philippines team handles the initial development review
- The US team provides final security validation
- 4-hour overlap windows for complex security discussions
- Emergency escalation during Philippines hours
- Next-day turnaround for most security reviews
Full Scale’s Philippines teams excel at this synchronized review process. Our developers start work at 8am PHT, perfectly overlapping with US West Coast afternoons. This positioning makes secure code review for distributed teams seamless.
The protocol maximizes the Philippines-US time advantage:
- Morning overlap (8-10am PHT / 5-7pm PST): Sprint planning and security briefings
- Philippines day shift: Active development and initial reviews
- Evening overlap (5-7pm PHT / 1-3am EST): Handoffs and urgent reviews
- US day shift: Final security validation and merge approvals.
The protocol includes specific security checkpoints for each review stage. First reviewers focus on obvious vulnerabilities and code structure. Second reviewers verify security assumptions and test edge cases thoroughly.
Layer 3: Continuous Security Monitoring
Real-time dashboards display security metrics across all timezones. Automated alerts notify teams of security-flagged code immediately. Weekly cross-zone security meetings ensure protocol alignment and knowledge sharing.
Essential monitoring components for distributed team security protocols:
- Real-time security dashboards
- Automated vulnerability alerts
- Behavioral anomaly detection
- Weekly security sync meetings
- Monthly security metrics review
- Quarterly security training updates
Our monitoring catches what automated tools and reviews might miss. Behavioral analysis identifies unusual code patterns across distributed teams. This final layer provides defense-in-depth for secure code review for distributed teams.
Full Scale’s security operations center continuously monitors all client repositories. Our Philippines-based security team provides 24/7 coverage at a cost-effective rate. This approach delivers enterprise-level security at startup-friendly prices.
With the framework established, implementation becomes straightforward. The following guide walks through each setup phase step-by-step. Your team can achieve enterprise-grade security in just 30 days.
Implementation Guide: Setting Up Your Secure Review Process
Transform your asynchronous code review security in 30 days. Our step-by-step approach minimizes disruption while maximizing protection. Each phase builds security muscle memory across your distributed teams.
Step 1: Tool Stack Configuration
Configure your code review security tools for maximum automation. Integration takes less than one week with proper planning. Most tools offer free tiers perfect for initial implementation.
Security ROI Calculator
Calculate your potential savings with automated security reviews
This calculator demonstrates typical security cost reductions from automation. Most teams see 85% fewer security issues reaching code review. The ROI typically exceeds 400% within the first year.
Essential configurations for secure code review for distributed teams:
- Webhook integrations for real-time alerts
- Branch protection rules enforcing security reviews
- Automated status checks before merge
- Security scanning in the CI/CD pipeline
- Centralized security dashboard access
Full Scale helps configure these tools for our staff augmentation clients. Our DevOps team in Cebu specializes in security tool integration. Secure code review for distributed teams becomes effortless with proper tooling.
Step 2: Process Implementation
Roll out security protocols gradually across your distributed teams. Start with pilot teams in each timezone for proof of concept. Scale to full implementation once initial metrics prove success.
Implementation timeline for remote code review security:
- Week 1-2: Tool setup and configuration
- Week 3-4: Security champion training
- Week 5-6: Parallel testing phase
- Week 7-8: Full rollout and optimization
Full Scale’s implementation methodology comes from deploying across 60+ clients. Our Philippines teams often serve as pilot groups for new protocols. Their feedback shapes the final secure code review for the distributed teams process.
Step 3: Access Control Setup
Define clear ownership for security-critical code paths using CODEOWNERS. Implement branch protection rules requiring security team approval. Create escalation paths for emergency security patches across timezones.
# Example CODEOWNERS file for secure code review for distributed teams
# Security-critical paths require security team review
/api/auth/ @security-team @regional-lead
/database/ @security-team @senior-dev
/payment/ @security-team @compliance-lead
/infrastructure/ @devops-team @security-team
# Regional security champions
*.php @philippines-security @us-security
*.py @eastern-europe-security @us-security
This structure ensures security expertise reviews all critical code changes. Regional champions provide timezone coverage for urgent reviews. Emergency patches follow expedited paths while maintaining security standards.
Even with perfect implementation, teams face common resistance points. The following challenges appear consistently across organizations. Here’s how to overcome each one effectively.
Overcoming Common Implementation Challenges
Resistance to new security processes is natural but manageable. Address concerns directly with data and pilot results. Show teams how automation actually speeds up their workflow.
Challenge 1: “This Will Slow Us Down”
Teams fear security reviews will delay feature delivery significantly. Reality shows automated checks run parallel to development work. Our clients report 40% faster overall delivery after implementation.
Evidence that secure code review for distributed teams accelerates development:
- 73% reduction in security-related rework
- 40% faster overall feature delivery
- 85% fewer production hotfixes needed
- 2x developer productivity improvement
- 90% reduction in security debt
Full Scale’s data from 200+ developers proves this consistently. The Philippines teams initially worried about additional process overhead. After implementation, they ship features 2x faster with fewer bugs.
Challenge 2: “Our Offshore Team Lacks Security Training”
Security knowledge gaps exist but are quickly closeable through training. Weekly security champion meetings build expertise across all regions. Recorded training libraries ensure consistent knowledge transfer between zones.
Full Scale’s approach to building security expertise:
- Mandatory security onboarding for all developers
- Weekly security champion meetings
- Recorded training library access
- Hands-on security labs
- Mentorship from senior security engineers
Our Cebu training center graduates security-conscious developers consistently. The key is making security part of daily development culture. Secure code review for distributed teams succeeds through continuous education.
Challenge 3: “We Can’t Afford These Tools”
One security breach costs more than five years of tools. Free tiers of essential tools provide 80% of the needed functionality. Start small and scale tool investment as ROI becomes clear.
Free security tools for distributed team security protocols:
- GitHub’s built-in security features
- SonarQube Community Edition
- OWASP Dependency Check
- GitGuardian’s free tier
- Dependabot (free for public repos)
Full Scale negotiates enterprise pricing for our client partnerships. Volume discounts make enterprise tools affordable for growing companies. Secure code review for distributed teams doesn’t require massive investment.
Theory becomes reality through real implementation. Our FinTech client’s transformation demonstrates the framework’s power. Their results show what’s possible with committed execution.
Real Results: Full Scale Client Case Study
A FinTech startup struggled with distributed team security vulnerabilities. They operated across the US, the Philippines, and Eastern Europe timezones. Previous security incidents cost them $120,000 in direct remediation alone.
The Implementation
We deployed our 3-layer security framework over six weeks systematically. Zero additional headcount was required for security coverage. Total tool investment came to $15,000 annually for 50 developers.
Implementation highlights for their global team code review process:
- Security champions from Full Scale’s Cebu office
- Custom dashboards for executive visibility
- Automated compliance reporting
- Zero-downtime deployment
- Seamless integration with existing workflow
The implementation included real-time metrics showing improvements weekly. Stakeholders saw immediate value from the security investment. Secure code review for distributed teams became second nature quickly.
The Results
Zero security vulnerabilities reached production in 12 months post-implementation. Security-related code review time dropped by 73% through automation. The team achieved 100% SOC2 compliance within four months.
| Metric | Before | After | Improvement |
| Production Vulnerabilities/Month | 8-12 | 0 | 100% |
| Review Time (hours) | 15 | 4 | 73% |
| Security Incident Cost | $120K/year | $0 | 100% |
| Compliance Status | Non-compliant | SOC2 Certified | Achieved |
| Developer Satisfaction | 62% | 94% | 52% |
These results reflect consistent patterns across our client implementations. Security automation eliminates most manual review overhead immediately. Compliance becomes achievable through standardized processes and audit trails.
Key success factors in their transformation:
- Executive buy-in from day one
- Security champions in each timezone
- Automated tools reduce manual work
- Clear metrics tracking progress
- Regular team training sessions
The client’s Philippines team particularly embraced the new security culture. They became security advocates, suggesting process improvements regularly. Secure code review for distributed teams transformed their development approach entirely.
Success stories inspire, but practical roadmaps enable action. Follow this 30-day plan to transform your security posture. Each milestone builds toward comprehensive protection.
Your 30-Day Security Transformation Roadmap
Transform your code review security protocols in one month. Each phase builds essential security infrastructure progressively. By day 30, you’ll have enterprise-grade distributed team security.
Days 1-10: Foundation
Audit current security gaps across all timezones systematically. Select security tools based on your tech stack requirements. Draft security review guidelines with input from all regions.
Foundation phase checklist for offshore development security:
- Document current review processes
- Identify security gaps and risks
- Select appropriate security tools
- Draft initial security guidelines
- Assign regional security champions
Full Scale provides security audit templates for this phase. Our consultants help identify your specific vulnerability patterns. Secure code review for distributed teams starts with understanding current risks.
Days 11-20: Implementation
Train security champions in each timezone on new protocols. Configure automated security scanners for your repository platforms. Create unified security dashboards visible to all team members.
Implementation phase priorities:
- Configure automated security tools
- Train security champions
- Set up security dashboards
- Create a documentation wiki
- Run pilot security reviews
Focus on quick wins during this implementation phase. Automated dependency scanning often catches numerous vulnerabilities immediately. These early victories build team confidence in secure code review for distributed teams.
Days 21-30: Optimization
Run the first cross-zone security review using the new processes. Gather metrics on review times and vulnerability detection rates. Iterate based on team feedback and initial results.
Optimization phase activities for asynchronous code review security:
- Collect performance metrics
- Gather team feedback
- Refine security processes
- Document best practices
- Plan ongoing improvements
The optimization phase reveals process improvements through real usage. Teams discover workflow adjustments that enhance security without adding friction. Secure code review for distributed teams evolves to match your culture.
Security Without Borders
Stop treating distributed team security as an unavoidable liability. The right framework transforms global teams into security advantages. You gain 24/7 coverage, diverse perspectives, and continuous threat detection.
Remote code review security requires intention, not perfection. Your team’s location matters less than your security processes. With proper protocols, offshore teams often exceed onshore security standards.
Why Full Scale Makes Secure Code Review for Distributed Teams Effortless
Full Scale specializes in building security-first distributed development teams. Our 200+ developers across the Philippines undergo rigorous security training. We’ve implemented these exact protocols across our own teams first.
Our advantages for secure code review implementation include:
Pre-trained Security Champions
- Every Full Scale team includes certified secure coding developers
- Seamless integration with existing security protocols
- No additional training investment required
- Immediate security expertise available
24/7 Security Coverage Built-In
- Philippines offices span multiple cities with overlapping shifts
- Natural timezone coverage eliminates review gaps
- Your code stays protected around the clock
- Emergency response teams are always available
Enterprise Tools at Startup Prices
- Volume licensing reduces security tool costs by 60%
- Pre-optimized tool configurations included
- Enterprise-grade scanning at affordable rates
- No setup or configuration headaches
Proven Security Track Record
- Zero security breaches across 60+ implementations
- 95%+ security audit pass rates maintained
- SOC2 compliance achieved within 90 days
- Continuous security training programs
Full Scale transforms secure code review for distributed teams from challenge to advantage. Our battle-tested processes eliminate security risks while accelerating development. Let us show you how security and speed work together.
Secure Your Distributed Development Today
FAQs: Secure Code Review for Distributed Teams
How long should a secure code review for distributed teams take?
Automated security checks complete in 2-4 hours for most codebases. Human security review should finish within 24 hours across zones. Emergency patches follow expedited 4-hour review protocols using our distributed team security protocols.
What tools are essential for distributed team security protocols?
Minimum requirements include GitHub/GitLab with security features enabled. Add one SAST tool like SonarQube for code analysis. Include dependency scanning via Snyk/Dependabot and secrets detection through GitGuardian for comprehensive remote code review security.
How do you handle emergency security patches across timezones?
Implement security escalation protocols with designated champions per zone. Emergency patches require one senior reviewer’s approval following simplified checklists. All emergency changes undergo full review within 48 hours to maintain secure code review for distributed teams standards.
Can Philippines’ offshore teams maintain US security standards?
Absolutely. Full Scale’s Philippines teams exceed US security standards consistently. With proper training and tools, location becomes irrelevant to security outcomes. Our SOC2 certified teams prove offshore development security equals or exceeds onshore standards daily.
What’s the minimum team size for implementing secure code review for distributed teams?
Teams as small as 5 developers benefit from structured security reviews. The framework scales from startups to enterprises seamlessly. ROI increases with team size but remains positive even for small teams using our global team code review process.
How much does implementing asynchronous code review security cost?
Initial tool investment ranges from $0 (free tiers) to $25 per developer monthly. Full implementation including training costs approximately $5,000-15,000 total. Compare this to average breach costs of $120,000+ to see why secure code review for distributed teams pays for itself immediately.



